Exploiting JWT

Stealing JWT
JSON Web Tokens (JWTs) are widely used for authentication and authorization in web applications. However, they can be vulnerable to various attacks that can result in JWT theft. Some common methods used to steal JWTs in a web application include:
- Cross-Site Scripting (XSS): XSS attacks involve injecting malicious scripts into web pages viewed by other users. If a web application is vulnerable to XSS, an attacker can inject JavaScript code that steals the JWT from the victim’s browser, typically by accessing the token via the DOM (Document Object Model).
- Cross-Site Request Forgery (CSRF): CSRF attacks trick authenticated users into unknowingly making requests on behalf of the attacker. If a CSRF vulnerability exists in a web application, an attacker can create a malicious page or link that, when clicked by a victim, performs actions that expose the JWT to the attacker.
- Man-in-the-Middle (MitM) Attacks: In a MitM attack, an attacker intercepts the communication between a user and a web application. If the communication is not properly secured (e.g., lacking encryption or using insecure protocols), the attacker can capture the JWT as it traverses the network, giving them unauthorized access to the victim’s account.
- Server-Side Vulnerabilities: Exploiting vulnerabilities in the server-side code of a web application can lead to JWT theft. If there are flaws in the authentication or session management mechanisms, an attacker can manipulate or bypass the server-side code to retrieve or tamper with JWTs.
- Local Storage Vulnerabilities: If a web application stores JWTs in the browser’s local storage without proper security measures, an attacker with access to the victim’s device (e.g., via physical access or malware) can extract the JWTs from the local storage.
- Phishing Attacks: Phishing attacks involve tricking users into revealing their credentials or accessing malicious websites that mimic legitimate ones. By luring victims to provide their credentials, including their JWTs, attackers can gain unauthorized access to user accounts.
To mitigate the risk of JWT theft, the SOC will implement secure coding practices and follow best practices for JWT usage. This includes properly securing the application against XSS and CSRF attacks, implementing secure communication channels (e.g., TLS/SSL), employing strong server-side security measures, and validating and securing storage of JWTs on the client-side. Regular security assessments and staying updated on the latest security vulnerabilities and countermeasures are essential for safeguarding against JWT theft and other security risks.
Exploiting misconfiguration with JWT signature verification
Exploiting flawed JWT signature verification can lead to the bypassing of JWT-based authentication and authorization mechanisms. Here are some ways attackers may attempt to exploit such vulnerabilities:
- None Algorithm: The “none” algorithm is intended for use during development but should never be used in production. If a web application incorrectly accepts JWTs with the “none” algorithm, an attacker can craft a JWT without a signature, effectively bypassing the verification step.
- Weak or Predictable Keys: If the secret keys used for JWT signature verification are weak or predictable, attackers may attempt key guessing or brute-forcing techniques to uncover the key and forge valid signatures for arbitrary JWTs.
- Algorithm Confusion: Some JWT libraries may allow multiple signing algorithms, but the server-side verification logic could be misconfigured or flawed. Attackers can manipulate the JWT’s algorithm claim (alg) to exploit weaknesses or confuse the verification process, potentially tricking the server into accepting forged tokens.
- Algorithm Substitution: If a web application allows the algorithm to be specified within the JWT payload (header or claims), attackers can manipulate this value to substitute a weak or less secure algorithm during the verification process. For example, they could replace a stronger algorithm like HMAC-SHA256 with a weaker one like HMAC-SHA1.
- Key Confusion: In situations where multiple keys are used for JWT signature verification, attackers can attempt to exploit key confusion vulnerabilities. This involves tricking the server into using an unintended or compromised key for verification, thereby bypassing the actual intended key.
- Side-Channel Attacks: Attackers may explore side-channel attacks to gather information about the verification process, such as timing or error messages, in order to deduce weaknesses or exploit potential vulnerabilities in the signature verification mechanism.
- Key Injection: If an attacker gains unauthorized access to the server or its environment, they may inject their own key into the verification process or manipulate the key used for signature verification, enabling them to forge valid signatures for arbitrary JWTs.
To prevent these exploits, The SOC will implement secure JWT practices:
- Always use strong cryptographic algorithms for signing JWTs, such as HMAC-SHA256 or RSA-SHA256.
- Ensure the secret keys used for signing JWTs are securely generated, stored, and protected.
- Implement secure verification logic that properly checks the algorithm and performs robust signature verification.
- Regularly update and patch JWT libraries or frameworks to address any known vulnerabilities.
- Employ secure coding practices and conduct security assessments to identify and fix any implementation flaws in JWT handling and verification.
Prep for Battle
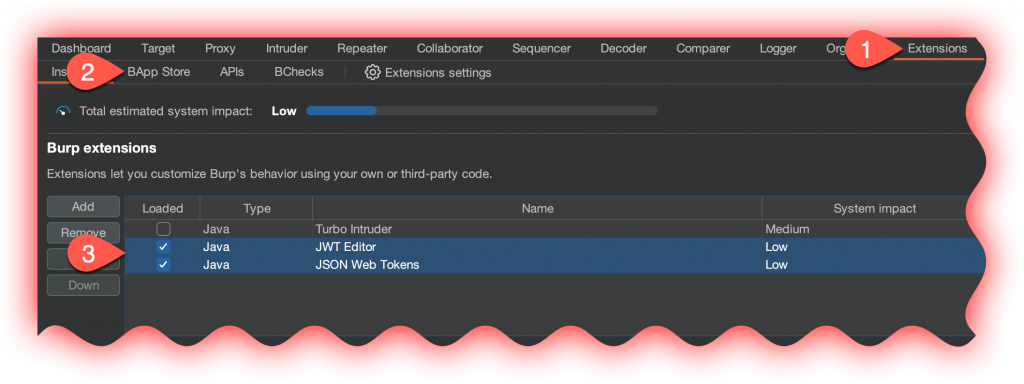
You will need to add the JWT extensions for Burp Suite Pro
- Open Burp Suite Pro
- Go to Extentions
- Open up BApp Store
- Scroll down to JSON Web Tokens
- Click Install
- Repeat for JWT Editor
Sources and Tools
CPE