SOC Analyst 1 (SA1)

SA1 Mission
Entry-level SOC analysts are responsible for monitoring security events, triaging alerts, and conducting initial investigations. They assist in incident response efforts and may perform basic security tasks such as vulnerability scanning and log analysis.
You are responsible for answering these questions for the SOC Team Leader (TL):
- What are we vulnerable to that can be exploited?
- Who is attacking us?
- What are the attackers trying to accomplish?
- What are the Indicators of compromise (IOC) that we should expect? How can we detect them?
As a SA1, you need monitor sensors. Then escalate to the Team Leader (TL)
[1] What are we vulnerable to that can be exploited?
For endpoints with utilizing CrowdStrike agents, utilize the Vulnerability Dashboard to track down vulnerable hosts. Remediate.
- Log into: Vulnerability Dashboard
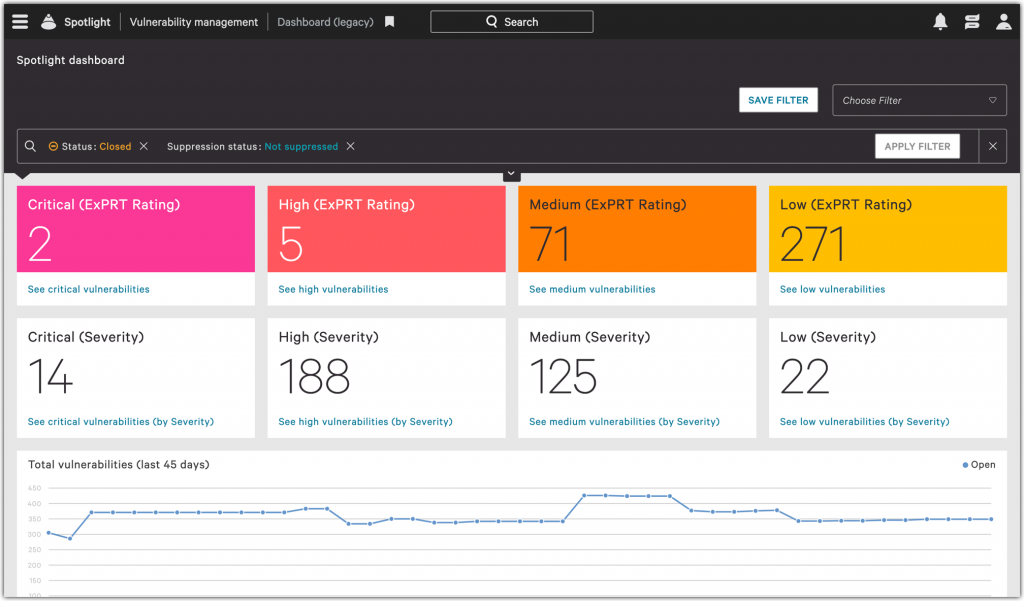
Check our repositories for vulnerable code
- Check snyk.io
- Check github.com and check dependabot
[2] Who is attacking us?
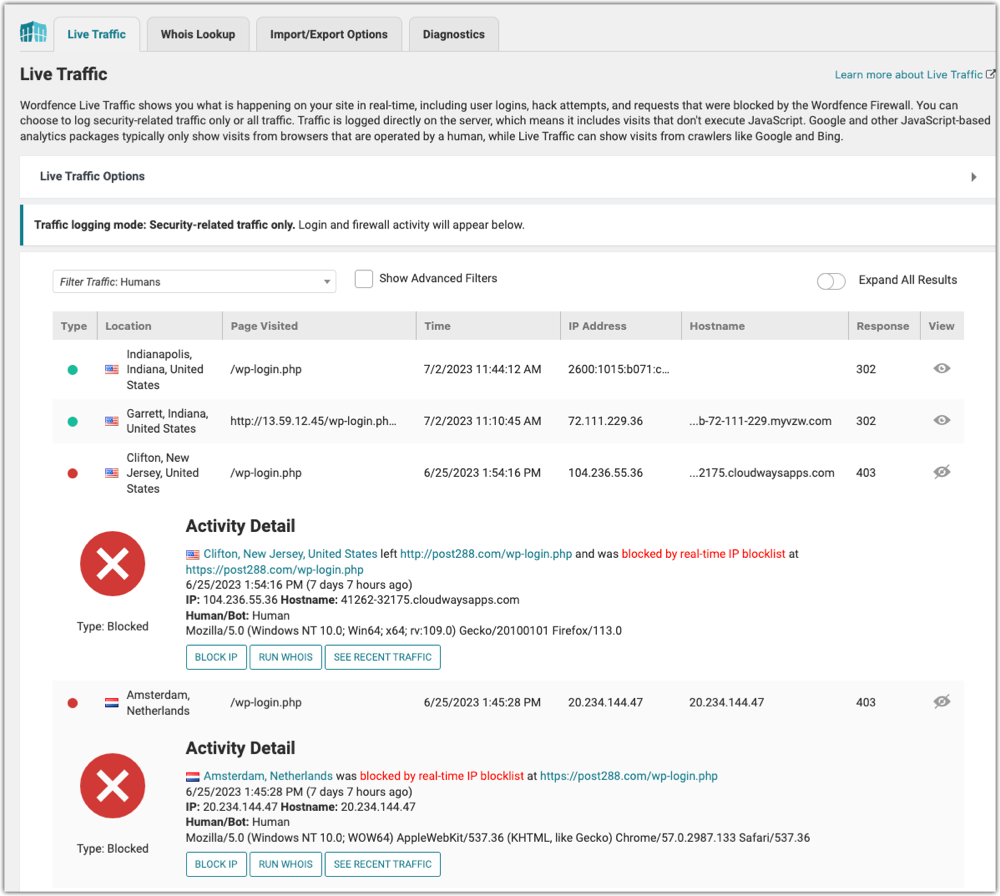
Use the WordPress plugins to check the traffic logs. This should provide answers for geolocation, source IP address (and sometimes hostname), HTTP Response code. You can perform Block IP, Run a Whois query, and See Recent Traffic.
- Wordfence > Tools > Live Traffic
- WP Activity Log > Log Viewer
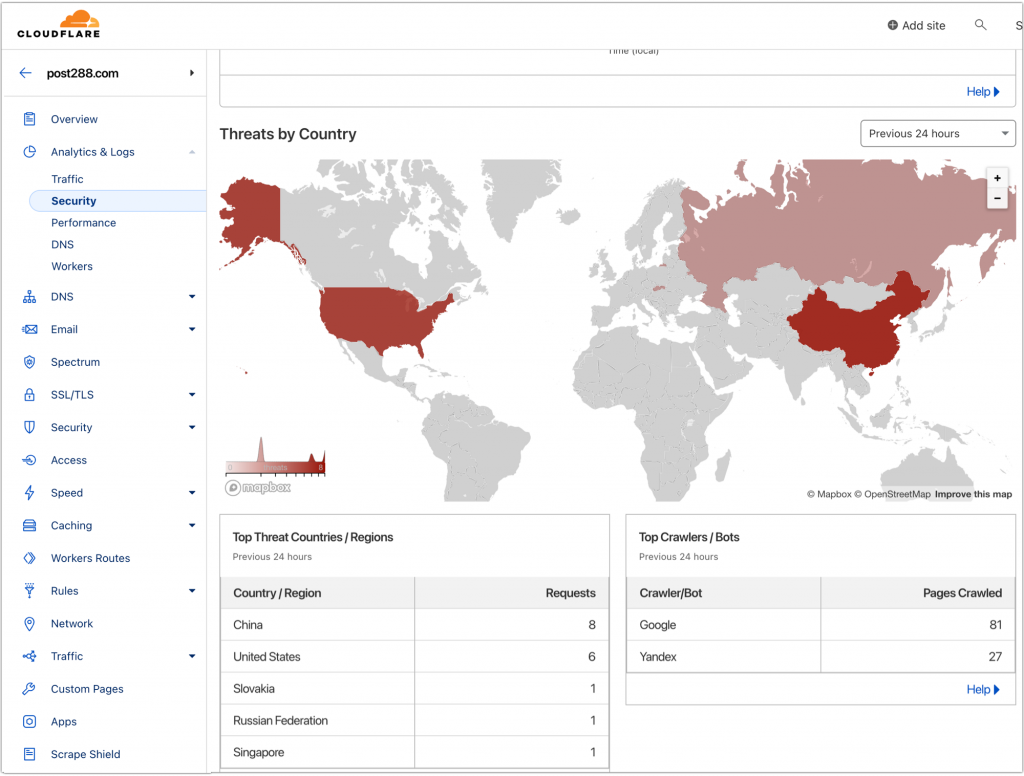
Check the Cloudflare WAF.
- Cloudflare > Analytics & Logs > Security
[3] What are the attackers trying to accomplish?
This may require multiple reviewing output from more than one tool to figure this out. Check the EDR, WAF,
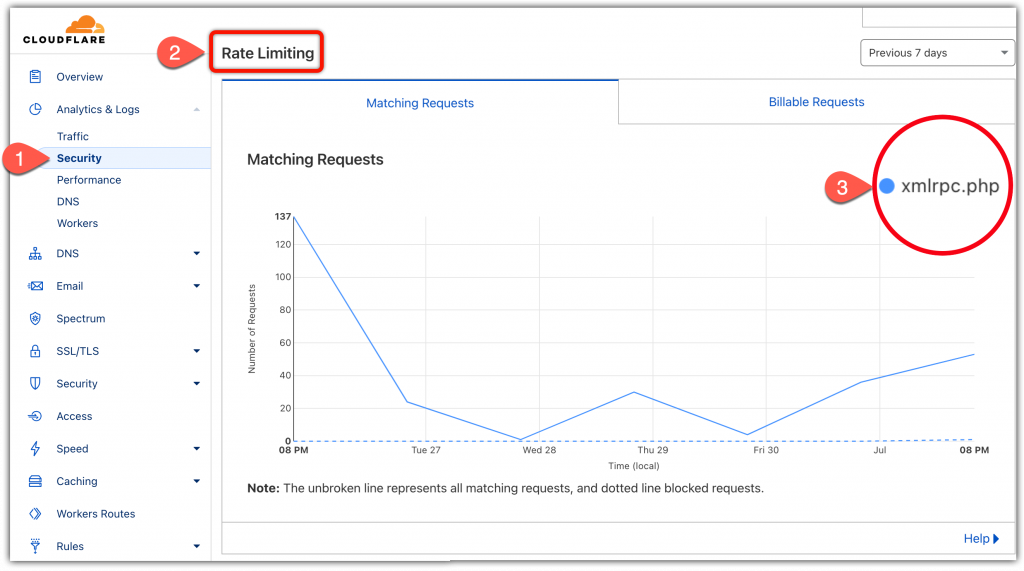
[3a] Are brute force attempts happening?
Checking the rate controls will provide this answer.
- Cloudflare > Security > Rate Limiting
[3b] What is being targeted?
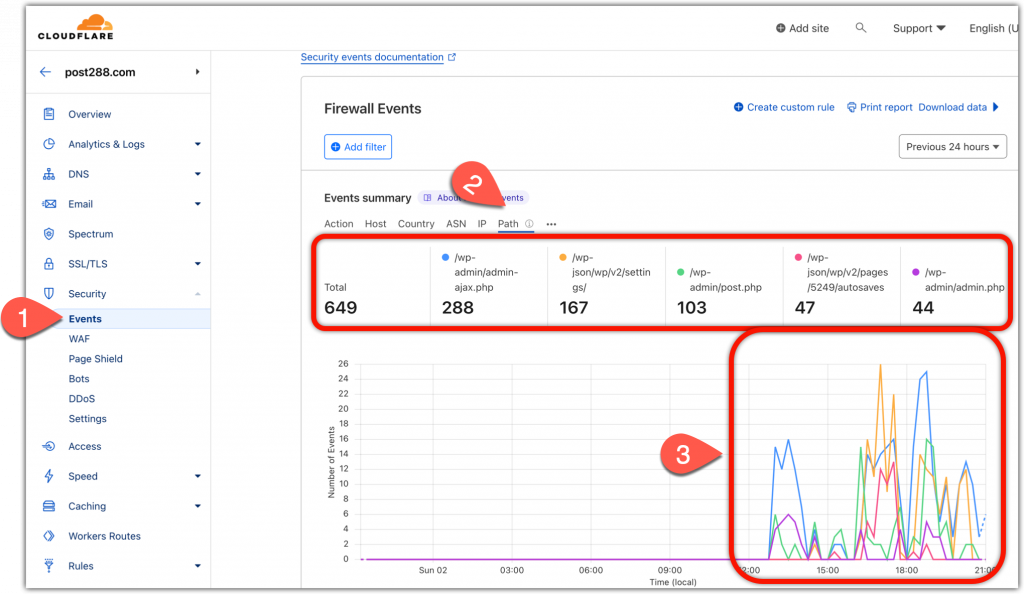
Check the WAF events to get some insight into what is happening.
- Cloudflare > Events > Path
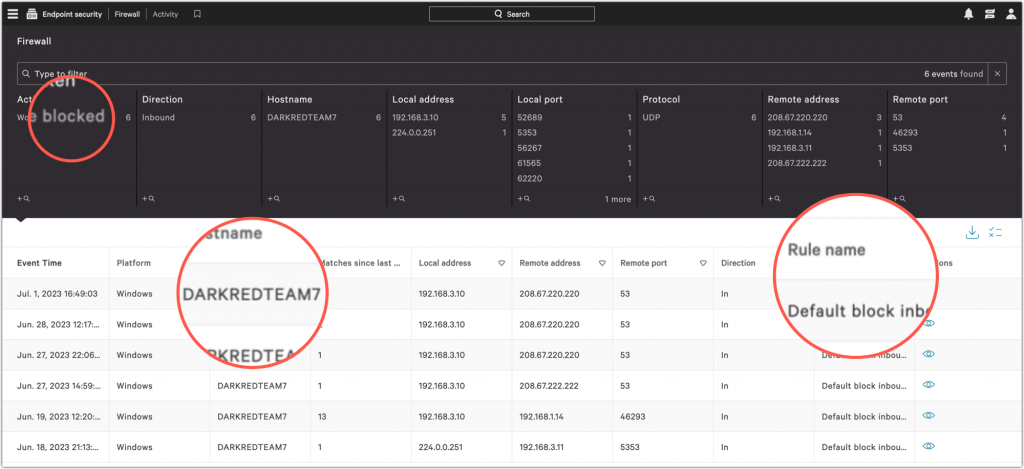
Check the CrowdStrike EDR Firewall Events.
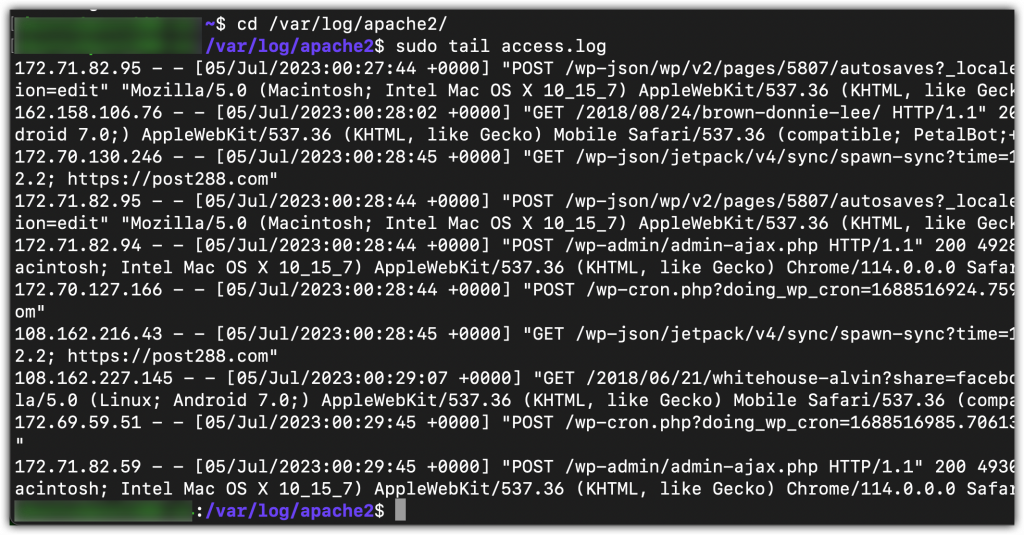
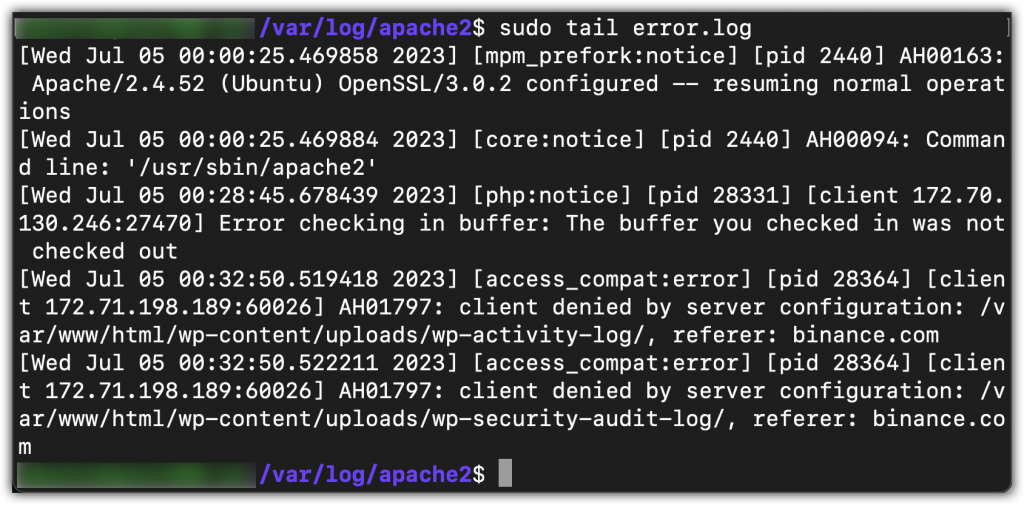
Check the host logs
- SSH into the server’s origin IP address, not the domain name. The domain name is only going to connect you into the CDN edge node (e.g. Akamai, Cloudflare, etc.).
cdtovarcdtologcdtoapache2catortaileach of theseaccess.log&error.log
Check the syslog file.
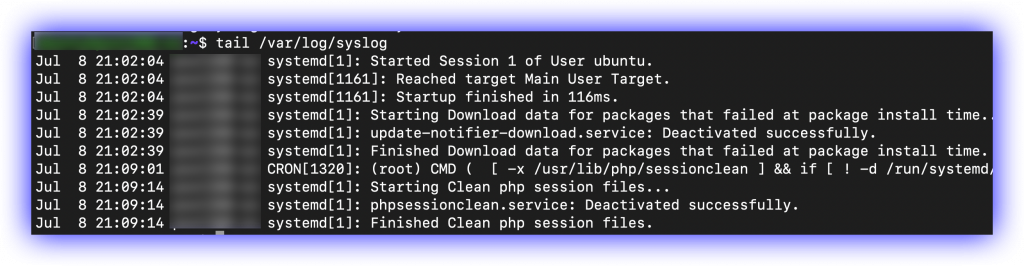
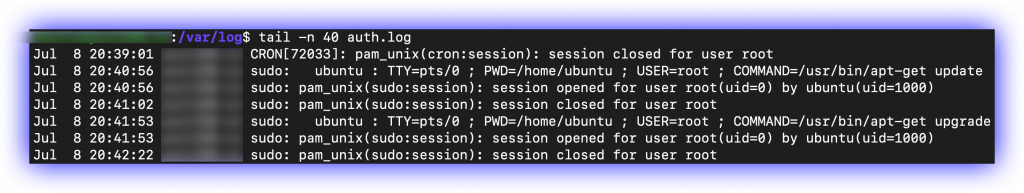
Check the auth.log file
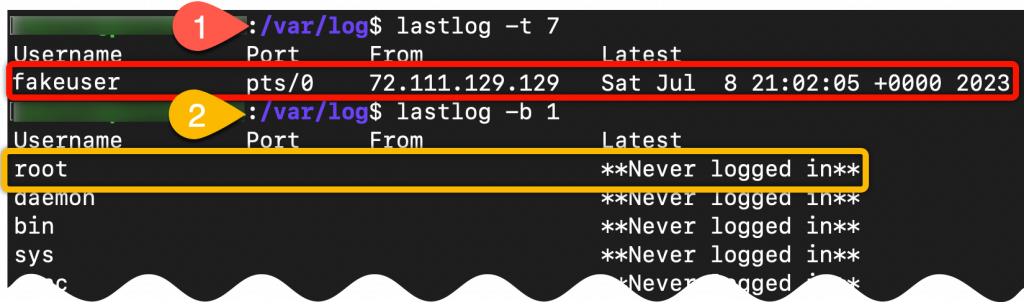
Use lastlog to see the login’s since the last server restart
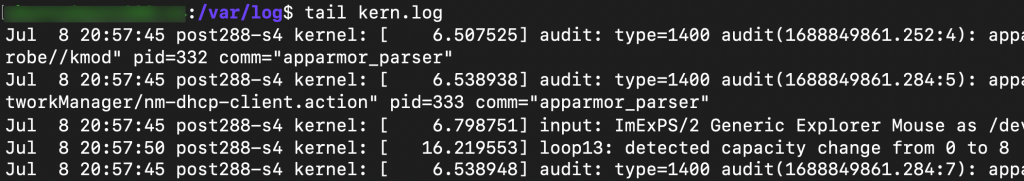
Check the kern.log file
[4] What are the indicators of Compromise (IOCs)?
To find indicators of compromise (IoCs) on a local network, there are several methods and tools that can be used. Here are some common ways to identify potential IoCs:
- Network Traffic Analysis: Monitor network traffic using network security tools, such as Intrusion Detection Systems (IDS) or Intrusion Prevention Systems (IPS). Look for suspicious or anomalous activities, such as unusual network connections, high data volumes to unexpected destinations, or communication on uncommon ports.
- Log Analysis: Review logs from network devices, servers, and applications for any signs of compromise. Look for abnormal login attempts, access to sensitive files or directories, or unusual system activities. Security Information and Event Management (SIEM) tools can assist in centralizing and analyzing logs from various sources.
- Endpoint Monitoring: Deploy endpoint protection solutions, such as antivirus or endpoint detection and response (EDR) tools, to monitor activities on individual devices. Look for indicators like the presence of malicious files, unusual processes or behaviors, or changes to system files and configurations.
- System File Integrity Monitoring: Implement file integrity monitoring (FIM) tools to detect any unauthorized modifications to critical system files or directories. Monitor changes to system binaries, configuration files, or critical application files that could indicate tampering or compromise.
- Network Intrusion Detection/Prevention Systems: Utilize network-based intrusion detection or prevention systems (NIDS/NIPS) to analyze network packets and detect known attack signatures or patterns. These systems can identify suspicious activities like network scans, port scans, or known exploit attempts.
- Vulnerability Scanning: Regularly conduct vulnerability scans on systems and network devices to identify any known vulnerabilities that could potentially be exploited. Exploited vulnerabilities can serve as indicators of compromise. Patch or mitigate identified vulnerabilities promptly.
- Threat Intelligence Feeds: Subscribe to threat intelligence feeds that provide information about known malicious IPs, domains, URLs, or file hashes. Compare network traffic, logs, or file hashes against these feeds to identify potential IoCs.
- Security Incident Response: Establish an incident response plan and team to quickly respond to and investigate potential security incidents. Train team members to recognize and respond to IoCs effectively. Document and analyze incidents to identify any IoCs and improve future response capabilities.
It’s important to note that IoCs can vary depending on the specific threat landscape and attack techniques prevalent at a given time. Staying informed about emerging threats, regularly updating security tools and signatures, and employing a defense-in-depth approach are crucial for effectively detecting and mitigating IoCs on a local network.
- OpenDNS – Look for potential C2 commo to known bad actors.
- Check Firewall NAT translation tables on NetGear (pfsense+), FortGate, Ubnt Security Gateway
- Check
netstat -anton suspected endpoints