Web Access Control
Cookie Attributes
Always store session information in cookies. Never pass session information as a query string parameter.
Domain attribute
The domain in which the cookie is valid.
Expires attribute
Determine when the cookie should be deleted.
expires=0 unless it’s a persistent cookie
HTTPOnly attribute
Stop JavaScript from reading the cookie values
HTTPOnly=true
Path attribute
Set pages and subfolders in which the cookie is available.
SameSite attribute
The SameSite attribute controls how cookies are sent for cross-domain requests. This attribute may have three values: ‘Lax’, ‘Strict’, or ‘None’. If the ‘None’ value is used, a website may create a cross-domain POST HTTP request to another website, and the browser automatically adds cookies to this request. This may lead to Cross-Site-Request-Forgery (CSRF) attacks if there are no additional protections in place (such as Anti-CSRF tokens).
Secure attribute
Avoid transmission over an insecure channel (e.g. HTTP)
Secure=true
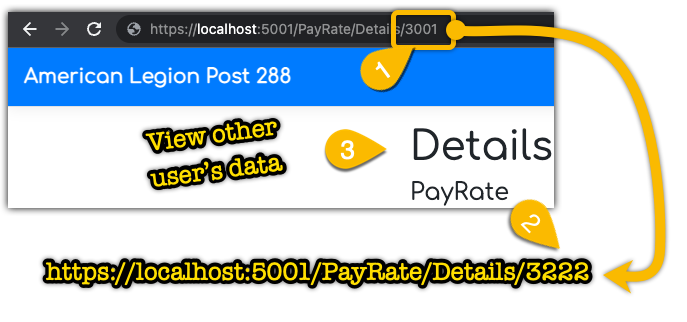
Indirect Object Reference (IDOR)
- Identify id numbers in URL (or scripts)
- Manually change them or use Burp to automatically increment
- View other user’s data
Path Traversal
What is Path Traversal?
An attacker constructs a pathname that is intended to access a file or directory that is located underneath a root web site directory. One of the most common path traversal techniques is the ../ sequence, which almost all operating systems interpret it as the parent directory of the current location. This is referred to as relative path traversal.
Absolute path traversal is different in that the pathnames such as /etc/apache2 start at the root directory and include all the subdirectories needed to get to the target.
Sometime the injection of a null byte NUL may allow an attacker to truncate a generated filename to widen the scope of attack. For example, the software may add .png to any pathname, thus limiting the attacker to image files, but a null injection may bypass this restriction.
Recommendations
- Don’t accept user input when using system calls if you don’t need to.
- If you must allow user input, make sure you sanitize it and make sure they aren’t allow to supply all parts of the path.
- Use indexes instead of parts of the file names when templating or using language files.
- Use
chrootjails (linux) and code access policies to deny access or modification of files.
Server Side Request Forgery (SSRF)
- Restrict requests made BY the server, only to destinations that it needs.
- Verify requested file type matches what is expected.
- Display a generic error to the use, but log details.
- Restrict requests to approved URL schemas